Best Of The Best Info About How To Detect A Ddos

Luckily, loggly has a tool for anomaly detection.
How to detect a ddos. This guide will cover fundamental aspects of ddos attacks and focus on advanced methods for their. In the trends tab toolbar, you’ll find the option to view anomalies. While there’s no one way to detect a ddos attack, there are a few signs your network is under assault:
Click “find anomalies” and you’ll see a screen. Attack surface reduction, threat monitoring, and scalable ddos mitigation tools. You see a surge in web traffic, seemingly out of nowhere, that’s coming.
Unfortunately, the typical signs mentioned above can also be caused by other issues, some of them good. An cybersecurity attack at change healthcare—a subsidiary of unitedhealth group—that began wednesday has caused prescription delays and disruptions at a. (i) the different types of ddos attack detection.
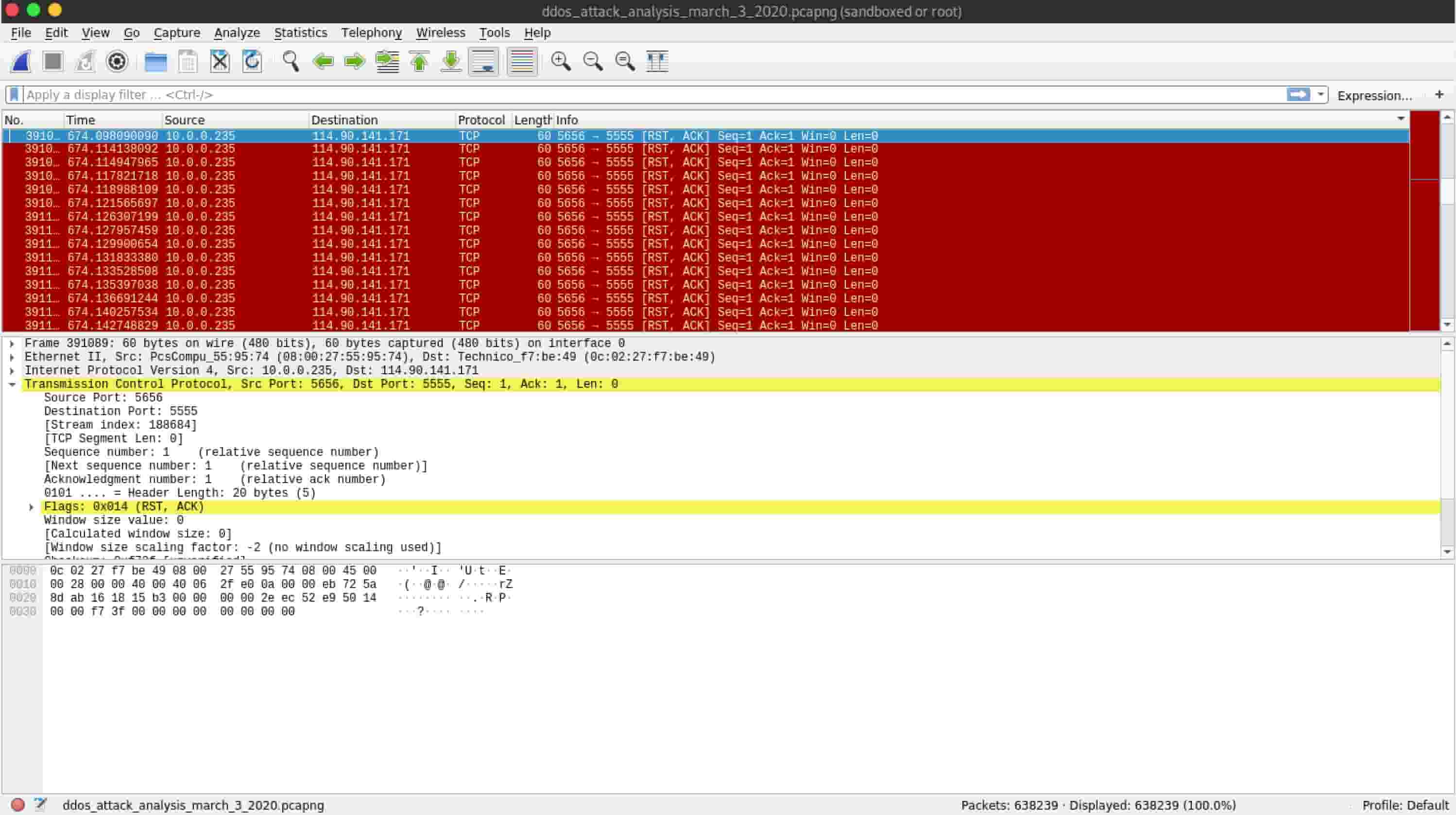
To detect attacks, both types need to be independently monitored; Distributed denial of service (ddos) attacks have increased in frequency and sophistication over the last ten years. In this video, we explore how to detect denial of service (dos) and distributed denial of service (ddos) attacks using the powerful network analysis tool, wi.
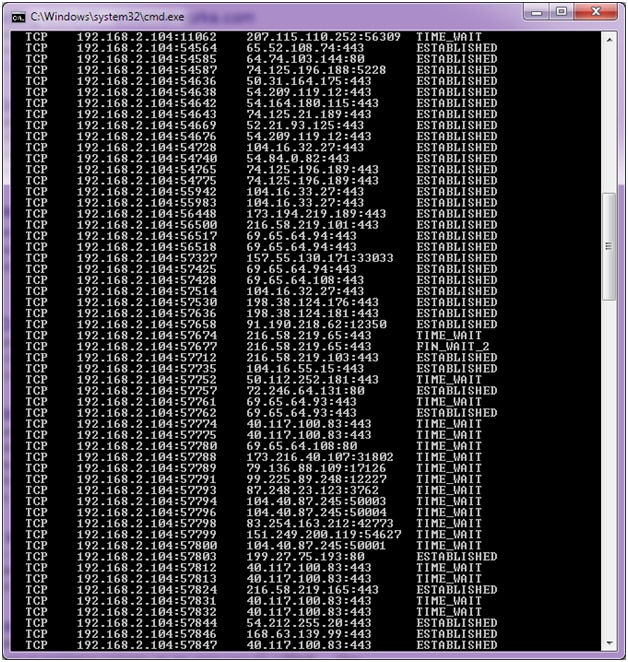
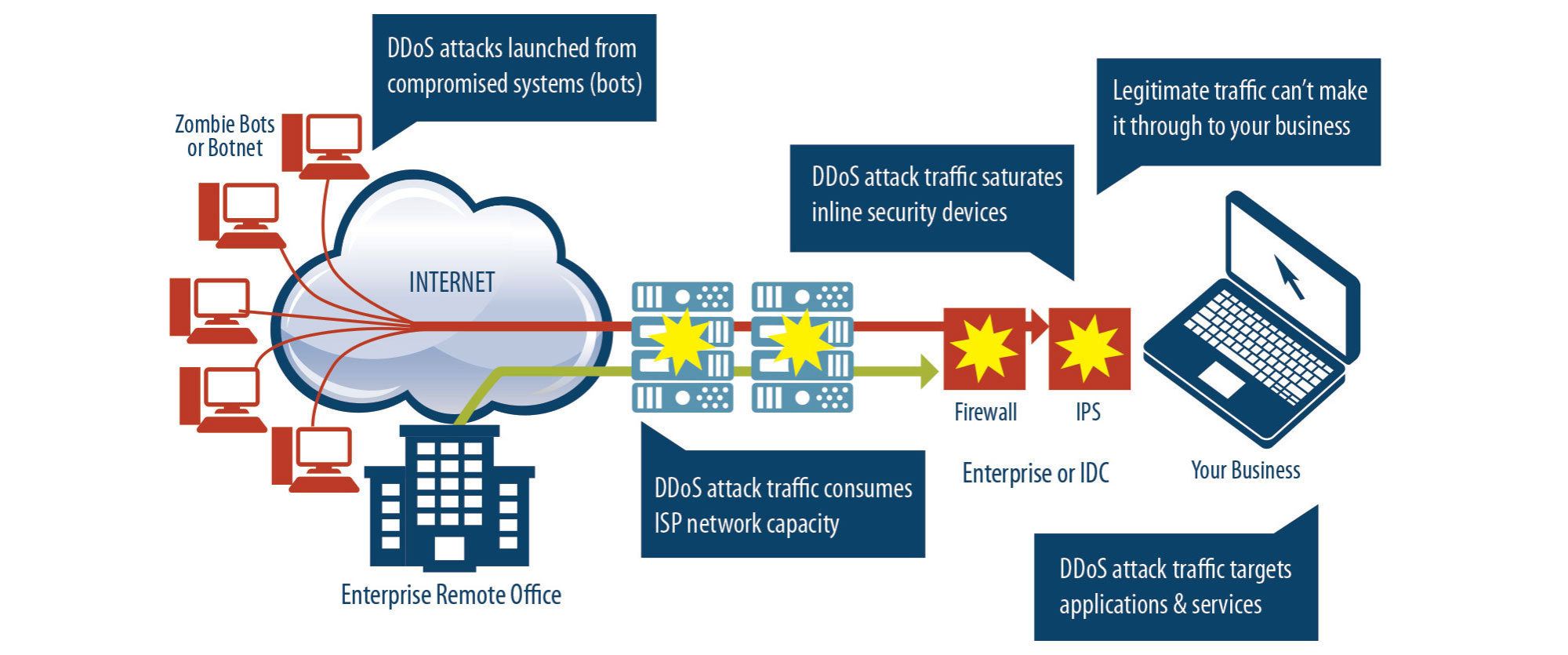
How to detect a ddos attack on a website imagine you notice something weird is happening to your site. The most effective way to mitigate a ddos attack is to know when it’s happening immediately when the attack begins. For example, if you are experiencing a sudden spike in web traffic and your site is slow to load, it could be due to increased legitimate user traffic such as a marketing campaign going viral or a mention.
Ddos attacks can be difficult to diagnose. Hackers launch ddos attacks to disrupt or put down a. According to a study by kaspersky lab, a ddos attack can cost an organization over $1.6 million — undoubtedly a massive sum for any enterprise.
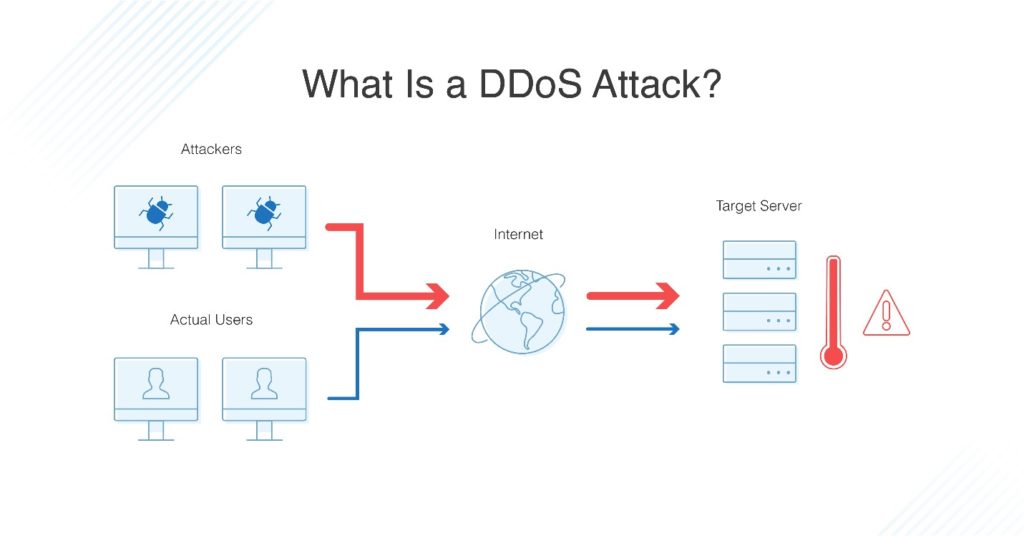
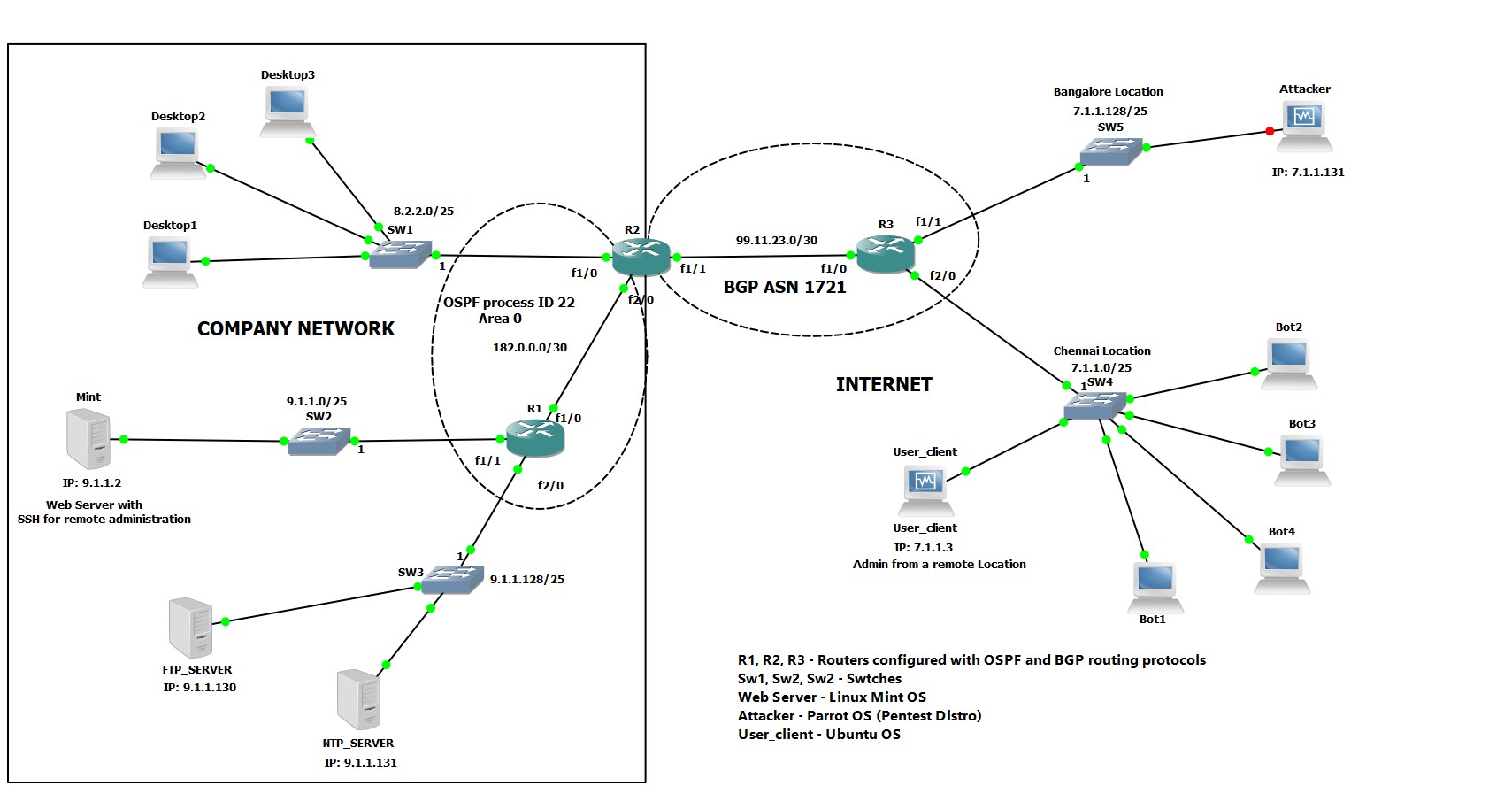
In this research, we have discussed an. A ddos attack is a denial of service (dos) attack that uses a botnet to flood the target with malicious traffic. Ddos attackers often leverage the use of a.
There are several clues that indicate an. At&t said late on thursday an outage that disrupted calls and text messages for thousands of u.s. Part of the challenge of defending against such.
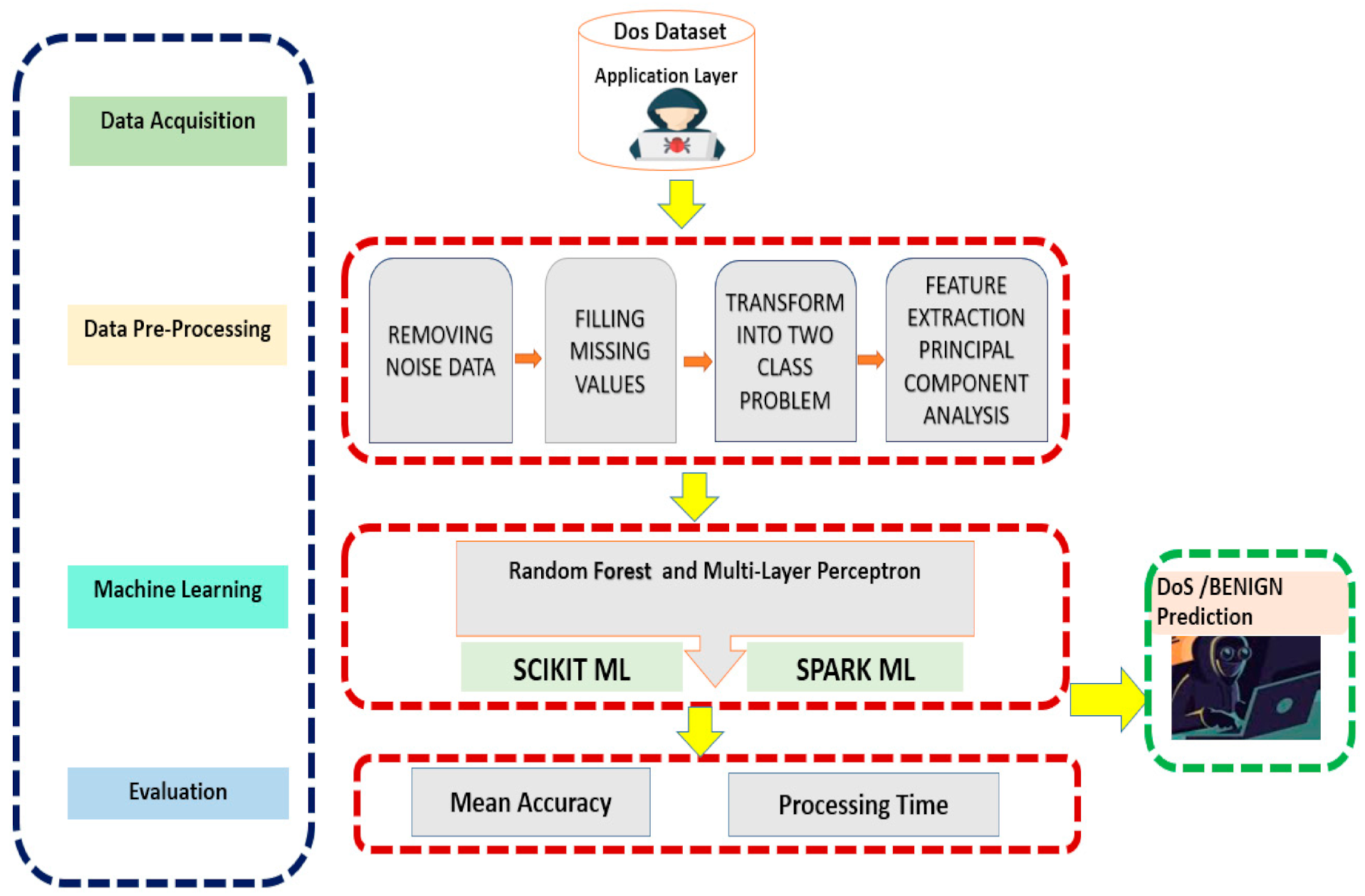
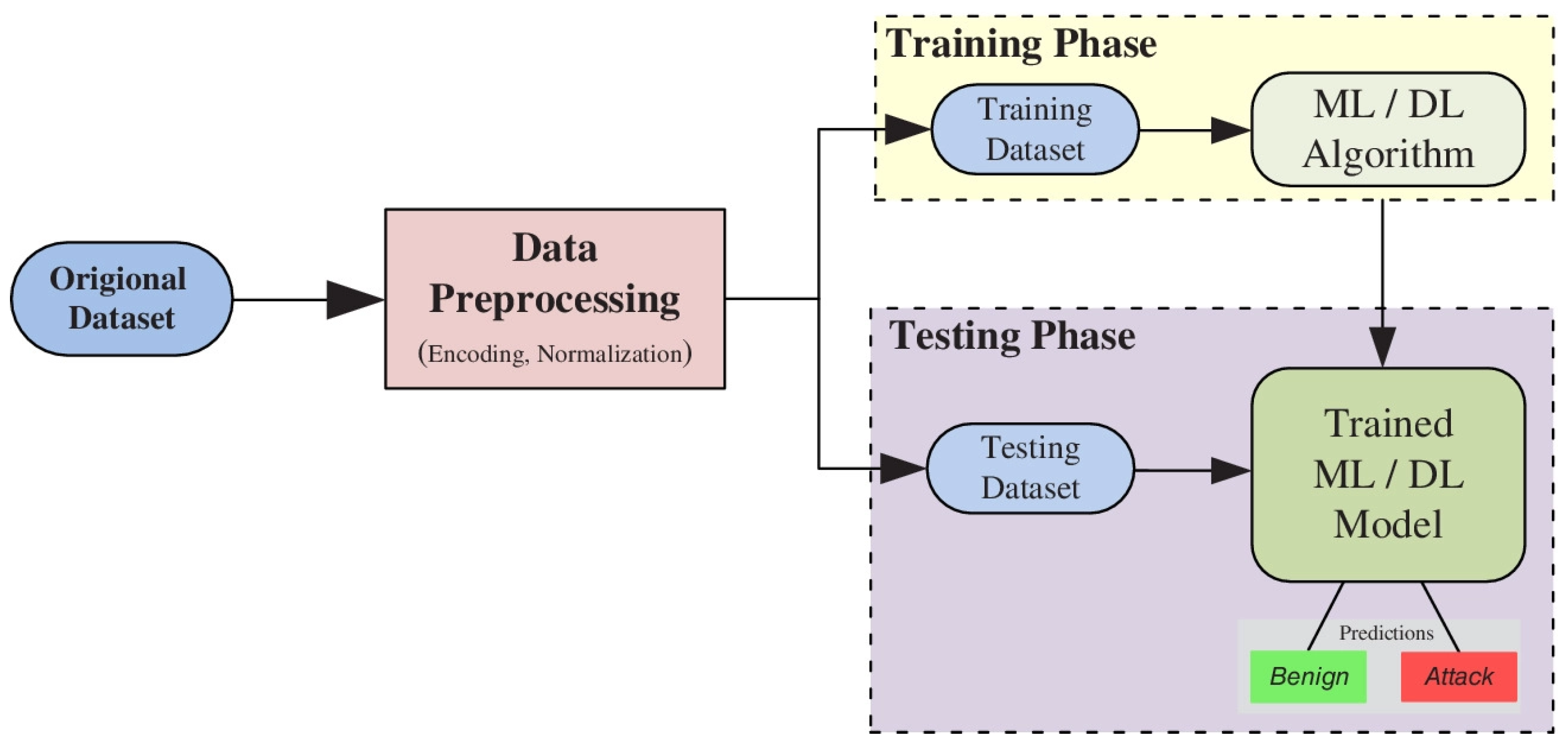
Early detection is key to mitigating these attacks effectively. We have analyzed the relevant studies and the results of the slr are categorized into five main research areas: And this is because to detect an attack, somebody has to analyze it first in order to produce a signature.
Here are seven key ways to enhance your. In the case of a ddos attack, the number of dns request packets will be considerably higher. Afterall, the attacks superficially resemble a flood of traffic from legitimate requests from legitimate users.





![【はイメージ】 Sds Calculus Module 8 Practical Applications [DVD] [Import](https://www.mdpi.com/applsci/applsci-13-03183/article_deploy/html/images/applsci-13-03183-g001.png)